Latest Posts
-
Set Up Always On Home Virtual Private Network (VPN) Using DD-WRT and a Linksys Router
 Last article I went over basic Home Network Security” let’s move on to something a bit more advanced- here’s how to set up an always on Home Virtual Private Network (VPN). What does a VPN do, and why do I need it? Simply put, a VPN creates a tunnel between two endpoints. The endpoints can be clients, such as your PC or even your smart phone. They can also be routers and servers. This tunnel creates a secure VPN connection that prevents interception of plain text and exploitation of the traffic. Also, to the outside world, you connection appears to be sourced at the VPN server, rather than your laptop. This allows you to do things like watch American shows on Hulu from outside the US- or access websites blocked by your normal internet access.
Last article I went over basic Home Network Security” let’s move on to something a bit more advanced- here’s how to set up an always on Home Virtual Private Network (VPN). What does a VPN do, and why do I need it? Simply put, a VPN creates a tunnel between two endpoints. The endpoints can be clients, such as your PC or even your smart phone. They can also be routers and servers. This tunnel creates a secure VPN connection that prevents interception of plain text and exploitation of the traffic. Also, to the outside world, you connection appears to be sourced at the VPN server, rather than your laptop. This allows you to do things like watch American shows on Hulu from outside the US- or access websites blocked by your normal internet access. -
Home Network Security 101

We (justifiably) spend a great deal of time and effort on Corporate Network Security, but what gets very little attention, is Home Network Security. Many of today’s modern home routers, by companies such as Linksys (now Cisco) and D-Link are a snap to connect, and now it is not uncommon to have multiple devices on a home network. Ten years ago a small office would have two or three computers and a T1 internet connection (1.54M down)- now you can see than many devices in many of your neighbors’ houses with ten times the bandwidth. Got an Xbox or a Tivo? You can put those on your home network too. Wireless throughput has increased more than 25 times from it’s introduction, and setting up a laptop where you sit in the backyard and work on the internet is nothing more than a 20 minute project. Although this article is not a comprehensive guide to home network security, I should mention that home wireless security is a HUGE issue- more on that later.
-
Old Fashioned Security and Brand New Technology
 If you’re a fan of Star Trek the Next Generation or classical theater, you might recognize Patrick Stewart- he has an interesting take on Twitter, email and the Internet. What’s fascinating is that he embraces some, but not all technologies to communicate. Selection of those tools seems to be very much a function of age. While email has long been a staple for myself and the engineers/consultants, some time ago I had to expand my cell plan to include text support. We’re certainly not up late at night talking about the latest movies or fashion, but it is very effective at sending a short update on a server outage or a meeting update. What I have discovered is that depending on the age group and business we’re working with, you can see a wide variety of communication tools in use- and the effective leader has to learn what works best for their team. At the end of the day, a simple paper filing system that is flexible enough to handle the workload without error will outperform a brilliant ERP system that is either improperly implemented, or not endorsed by employees and management.
If you’re a fan of Star Trek the Next Generation or classical theater, you might recognize Patrick Stewart- he has an interesting take on Twitter, email and the Internet. What’s fascinating is that he embraces some, but not all technologies to communicate. Selection of those tools seems to be very much a function of age. While email has long been a staple for myself and the engineers/consultants, some time ago I had to expand my cell plan to include text support. We’re certainly not up late at night talking about the latest movies or fashion, but it is very effective at sending a short update on a server outage or a meeting update. What I have discovered is that depending on the age group and business we’re working with, you can see a wide variety of communication tools in use- and the effective leader has to learn what works best for their team. At the end of the day, a simple paper filing system that is flexible enough to handle the workload without error will outperform a brilliant ERP system that is either improperly implemented, or not endorsed by employees and management. -
Travel Tips For Your Laptop, Part II
In the first part of the article, Travel Tips For Your Laptop, Part I, I went over how to get your computer ready for a trip. Now I’ll continue on with some of the tricks of the trade that the consultants and I have developed over the years to make traveling easier, and more painless. Let’s talk a little bit about luggage and gear.
-
Travel Tips For Your Laptop, Part I
 My consultants and I travel with a computer for living, and over the years we’ve come up with several travel tips for your laptop. Some technical, some not, all the product way too many passes through the security checkpoint. It’s not hard to get everything organized, you just need to do a bit of planning.
My consultants and I travel with a computer for living, and over the years we’ve come up with several travel tips for your laptop. Some technical, some not, all the product way too many passes through the security checkpoint. It’s not hard to get everything organized, you just need to do a bit of planning. -
Password Strength Checker
I remember running a security audit against one of our domains when I was in the military. We ran some utilities against the domain controllers and put together a list of the user’s passwords, and then used them in a presentation about security for the users. They were shocked when we put up the list. Here’s a list of 500 of the most common passwords (*Caution, some of these are obscene*)- if you see any of your passwords here immediately change them. They’re well known and the hackers start with this list. If you didn’t see your list and would like to check a password, try this password checker. And yes, change a couple of letters in your password before you put it in there - never give your passwords to anyone.
-
Disaster Recovery
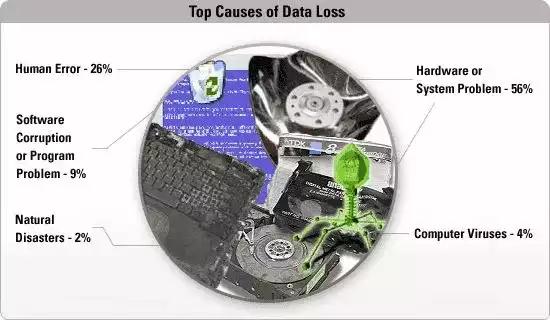
I’d like to take the time to talk about something that most people find boring, but is critically important when it comes to your computer, at work AND at home. Backups. They’re not fun. They’re not exciting. And the only time they really get a lot of attention is when:
-
Strategies for Avoiding and Removing Spyware
Over the last twenty years I’ve worked on computers in the military, IT service providers, businesses both large and small. The one major complaint they all have in common are viruses and spyware. It also happens to be number one on my “Family Tech Support” call list as well. The Anti-Spyware Coalition defines spyware as: